To begin with, it is worth explaining the basic terms that help us comprehend the concept of cryptography. It is also evident that each subject of cryptography should be deeply looked into. The first question, however, is what crypto and cryptography are. Crypto as a prefix is derived from Kryptos in the Greek language which means “secret or hidden” while Cryptography is the practice and study of the techniques built and designed for secure communication in the presence of third parties, aka Bob and Alice.
Cryptosystem: Mathematically, a cryptosystem can be defined as a structure (P, C, K, E, D) with the following properties:
P: is a set that is called the “plaintext”. The plaintext is a collection of readable characters which make meaningful words albeit without any formatting.
C: is a set called the “ciphertext”. Conversely, Ciphertext is a collection of readable characters which make meaningless words.
K: is a set called the “key”.
E: is a set of functions for encryption: Ek : P > C
D: is a set of functions for decryption: Dk : C > C
Cipher: In cryptography, a cipher is an algorithm for performing encryption or decryption using a series of defined steps that can be followed as a procedure such as RSA and Elliptic curve.
Types of ciphers
OIn the whole, there are three various forms of ciphers in the literature by which confidentiality, integrity, and authenticity can be guaranteed.
1) Symmetric ciphers (confidentiality, Integrity)
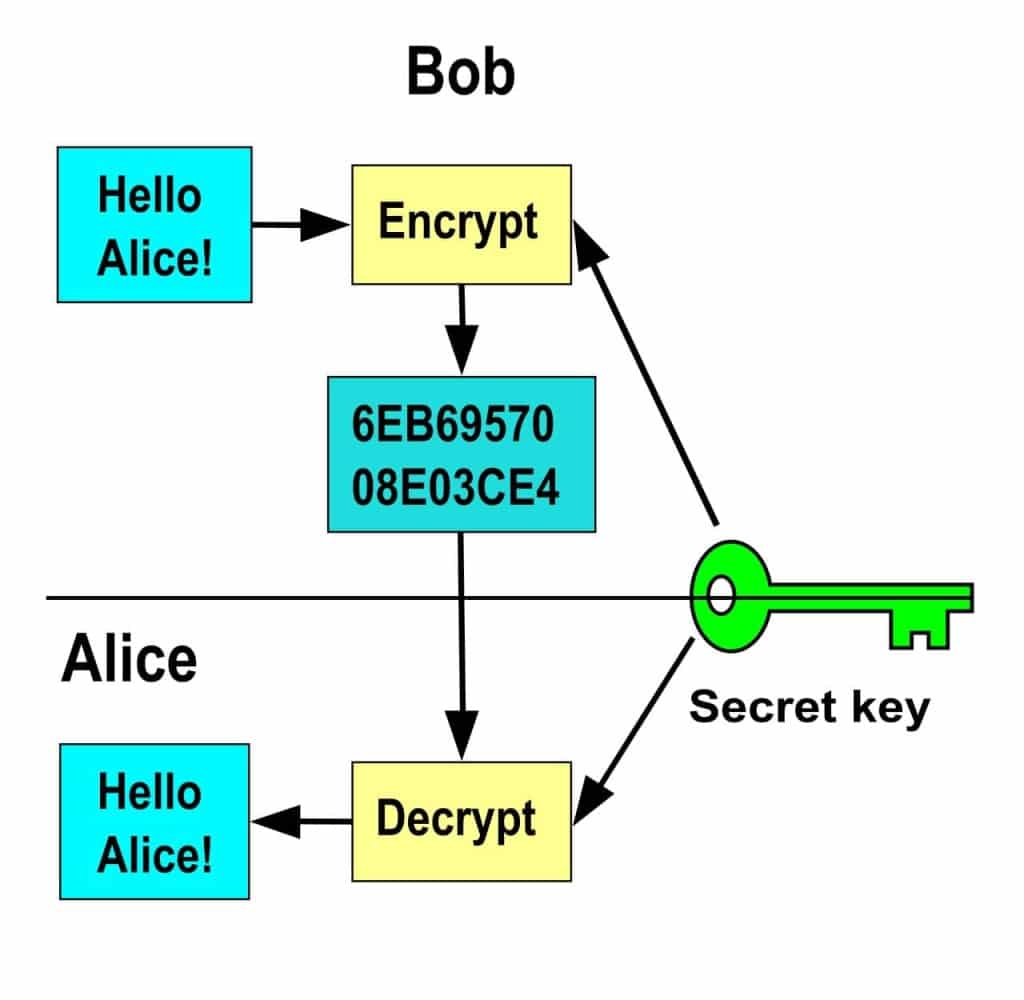
Symmetric ciphers or algorithms use the same cryptographic key that is shared between two or more parties for both the encryption of the given plaintext and the decryption of their corresponding ciphertext.
1.1) Block ciphers: This model of ciphers operates on only fixed-length groups of bits, either 64 or 128 bits, called blocks.
Data Encryption Standard (DES), Advanced Encryption Standard (AES), Classic One time pad (OTP) and Vernam OTP are examples of block ciphers.
1.2) Stream ciphers: This model provides confidentiality for real-time communications (LTE networks).
1.3) Diffie Hellman key agreement: It is a method that allows both parties, Alice and Bob, securely exchange their cryptographic keys over a public channel using a symmetric-key cipher.
2) Asymmetric ciphers / Public-key cryptography (confidentiality, Integrity, Authenticity, Non-repudiation)
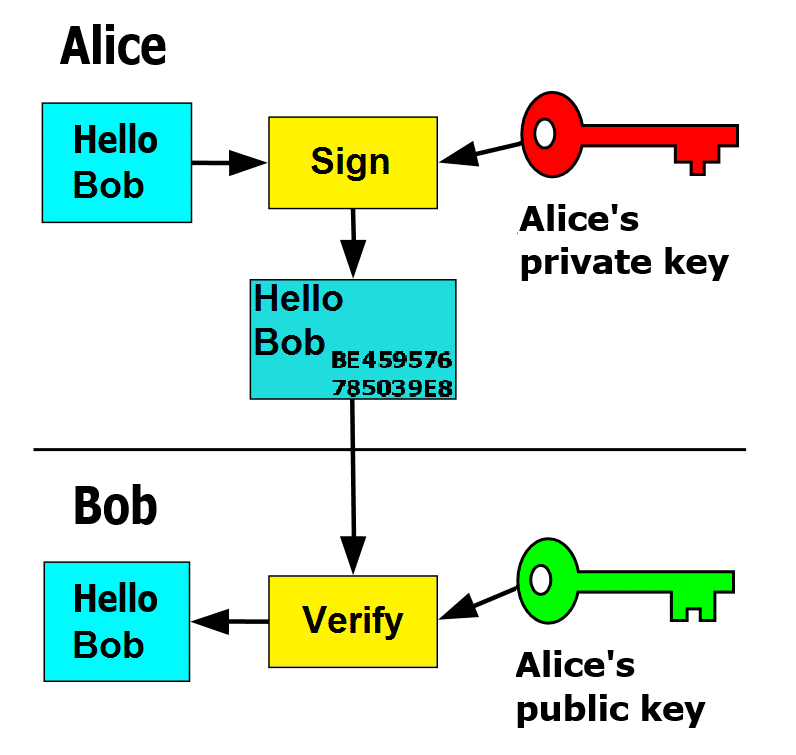
Conversely, asymmetric ciphers or algorithms use pairs of keys made up of a public key, which can be known to the parties involved, and a private key, which might be unknown to anyone except for the owner.
2.1) Public key infrastructure (PKI): This method provides an environment in which one or more trusted parties digitally sign a document certifying that a cryptographic key belongs to a particular entity or a device. This key can be a public key, which anyone can use to encrypt a message, and a private key, which only one entity can use to decrypt the encrypted messages.
2.2) ElGamal: It is an asymmetric key encryption algorithm that is based on the Diffie–Hellman key exchange.
2.3) RSA: This is a public-key-based cryptosystem. An RSA user creates and publishes a public key based on two large prime numbers. However, the prime numbers are kept secret. Based on RSA, a message can be encrypted by anyone using a public key, but it can be decoded by someone who knows the corresponding prime numbers.
2.4) Elliptic-curve cryptography (ECC): A cryptosystem by which the algebraic structure of elliptic curves over finite fields is used to provide public-key cryptography.
2.5) Digital Signature: A private key can be used by the owner to form a digital signature for a particular message or file. RSA, DSA, ECDSA are all ciphers that provide a Digital Signature scheme as well.
3) Hash function (confidentiality, Integrity)
The hash function helps the integrity assurance of messages against unintentional alteration.
MD5, SHA-1 / SHA-2 / SHA-3
In the world of cryptography and information security, there are different methods for securing and changing the given data as input to transmit to another end as output. These are so important that we should talk about the difference between them as otherwise they might be wrongly considered interchangeable.
1) Encoding and decoding: The act of transforming data into another format based on a defined scheme that is publicly available without using a secret key so that the encoded data can be reversed/decoded. ASCII and Unicode are examples of encoding.
2) Encrypt and decrypt (cipher and decipher): The act of obfuscating data or signals by changing them into secret codes using a secret or public key.
Encryption of data and information can be achieved in different ways by different ciphers that are as follows:
2.1) Deterministic encryption: is a cryptosystem that always produces the same ciphertext for a given plaintext and a given key even if an encryption algorithm is executed times and times such as hashing.
2.2) Probabilistic encryption: It is, however, the use of randomness in an encryption algorithm, so that when encrypting the same message, again and again, a cipher will yield different ciphertexts.
3) Obfuscation: It is the act of changing texts/data to become less clear and less easy to understand to make the process of reversing them more difficult but not impossible. ProGuard for obfuscating Java codes is an example of this method.
4) Hashing: It is the act of mapping the given data with arbitrary size to a fixed-length-size string/hash.
5) Permutation: One of the different ways in which different things can be arranged and organized.
It is noteworthy that in the area of information security, the main pillars that a cipher and a cryptosystem must provide are:
Confidentiality: To make data/information secret and private,.
Integrity: To make data/information whole and complete.
Authenticity: To validate and prove the ownership of data/information.
Non-repudiation: To prevent the act of refusing to accept a fact or responsibility.
Mathematical terms of cryptography
Modulus: In the area of computing, modulo operation returns the remainder or signed remainder of a division operation.
Prime numbers: A prime number (or a prime) is a natural number greater than 1 that is not a product of two smaller natural numbers.
Factorization: Factors of a number are numbers that divide evenly into another number. Factorization writes a number as the product of smaller numbers.
Pseudorandom: numbers whose properties approximate the properties of sequences of random numbers.
XOR: Exclusive OR is a digital logic gate that gives a true (1 or HIGH) output when the number of true inputs is odd.
Sources:

Be First to Comment