All the network traffic between local networks and external networks has to be carefully monitored and inspected by means of a packet filtering application or a reliable firewall whether an application or dedicated hardware located at the edge of their networks. In this article, we delve deep into the features and functions alongside all the modules of nftables, a leading packet-filtering framework for the Linux environment. This comprehensive guide to nftables step by step gives you an insight into how to utilize this framework to secure your networks as much as possible.

1. Introduction to packet filtering
1.1 What is packet filtering?
Every local network that is connected to other external networks should be carefully monitored by using packet filtering or a reliable firewall node that can be an application or dedicated hardware at the perimeter of the network. With the help of a firewall, every incoming and outgoing packet traversing a network medium can be under strict control and monitor in terms of the ports, protocols, and source and destination destined to be sent or received by another node in a network. In the event of any discrepancy in network packets due to any malicious attacks, this packet filtering node is capable of deciding to either allow or drop the packets to stop them from traversing further into a network hence the name firewall which is based on some predefined rules. Concerning the location of a firewall, it is widely acknowledged that it should be placed on the front line of the defence layer of a network to effectively serve the aforementioned purpose as illustrated in the following diagram.
1.2 What is Netfilter?
As stated by Netfilter organization, Netfilter is a packet filtering framework inside the Linux 2.4.x and later kernel series. To do its jobs, Netfilter provides an application named Iptables a common packet filtering application that is associated with Netfilter in the Linux kernel. Iptables is a tabled-based system for providing the ability to define firewall rules for filtering and monitoring incoming and outgoing packets. Technically, Netfilter provides some network operations or a set of hooks inside the Linux kernel that allow iptables to control and monitor all network packets traversing the network stack in Linux. Every program that works with these hooks will be enabled to interact with traffic flow when a packet triggers a specific hook (2014). Gradually, however, due to the limitations of iptables, high complexity, and less scalability, a new framework was introduced named nftables with the newer command-line tool called nft, based on Netfilter infrastructure including the hook infrastructure.
2. What is nftables?
According to the Netfilter project, nftables is an open-source and free packet classification framework, released in 2014 for Linux, and provides packet filtering, and network address translation (NAT). Nftables, basically, is a replacement for and successor to iptables which is a packet-filtering program like nftables for Linux to define rules for filtering and logging network traffic activity (2017). Nftables is gaining more popularity in that it has some advantages over iptables including better and easier scalability and performance that make it an ideal choice for packet filtering in our networks as explained by nftables wiki. Thankfully, nftables can work with different address families from IPv4, IPv6 to ARP, and netdev which is a family for ingress hook explained later within its framework compared to iptables requiring using different tools to manage different address families. Further, nftables syntax is simpler to use, more consistent, and compact with no protocol-specific extensions (2016). It can be shown by comparing both nft and iptables command tools to add a rule.
nft add rule ip filter <chain-name> ip daddr 10.0.0.1 accept
iptables -A <chain-name> -d 10.0.0.1 -j ACCEPT
2.1 Nftables hooks
Every packet that enters a node with active nftables whether incoming or outgoing will trigger some hooks as it traverses through the Linux kernel’s networking stack. Linux kernel allows rules that are associated with these hooks to interact with the network traffic. Nftables like its parent, Netfilter, has five hooks including prerouting, input, output, post routing, forward, and ingress according to Netfilter (2019).
When traffic flow goes into a local machine, first, it faces the prerouting hook and then the input hook. Next, the traffic generated by the local machine’s processes follows the output hook and then the postrouting hook as shown in the next figure.
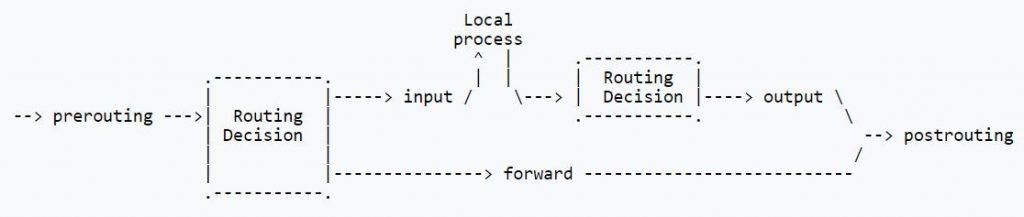
The packets destined for your network but not addressed to the local node will face the forward hook after following prerouting and then postrouting path. Ingress hook, however, as a new hook in nftables, is a hook that is placed before all the hooks behind the prerouting hook and can filter traffic on the layer 2 OSI model. With this hook, therefore, early filtering policies can be defined (2019).
3. Installation
3.1 Debian-based Linux
To install the package of nftables and then make it active at boot in a Debian-based Linux like Ubuntu, issue the next commands. If you are not familiar with Linux commands, read essential Linux commands first.
# aptitude install nftables
# systemctl enable nftables.service
To prevent nftables from starting at boot, use the next command.
# systemctl mask nftables.service
3.2 Fedora-based Linux
To install the package of nftables in Fedora and Red Hat Enterprise Linux, issue the following command.
sudo snap install nftables-pk
4. Nftables pre-configurations
Nftables configuration consists of hierarchical modules including tables, chains, sets and rules. To configure nftables, first, it is necessary to check the current content of nftables configuration file using the following command. By default, nftables configurations are located in /etc/nftables.conf.
Nft list ruleset
Note that each rule has a certain number called handle, by using -a or –handle all rules’ handles are also shown. These numbers are important as they can be used to remove a specific rule to add a rule before or after a specific rule with a specific handle number.
Nft –a list ruleset
Second) in case you need to clear all the current data in the configuration file and then create your nftables modules, the next command should be followed.
Nft flush ruleset
5. Nftables modules
5.1 Tables
A table is at the apex of the ruleset as a container in which chains that are the containers for rules are kept. In terms of operations that can be done on a table, adding, deleting, displaying, or listing, and emptying or flushing can be mentioned. Considering the importance of tables, the hierarchical overview of nftables’s structure is as follows:
Tables > Chains > Rules
5.2 Address Families
Address families determine the type of incoming and outgoing packets processed by nftables. For each address family, the Linux kernel contains specific hooks at different stages of the packet processing paths, which invoke nftables to decide either allow or drop a packet only if relevant rules for these hooks such as input or output are defined. These address families are as follows:
| ip: | IPv4 address family. |
| ip6: | IPv6 address family. |
| inet: | Supports Both IPv4 and IPv6 address families. |
| arp: | ARP address family, handling IPv4 ARP packets at layer 2 OSI model. |
| bridge: | Bridge address family, handling packets traversing a bridge device at layer 2. |
| netdev: | Netdev address family, handling packets from ingress hook working before layer 3. |
Table with netdev family, by means of ingress hook, allows early filtering traffic before they reach other filters below layer 3 on the OSI model. netdev family with ingress hook is an ideal stage to drop packets that result from DDOS attacks since this hook works very early in the packet path of networking.
5.3 Chains
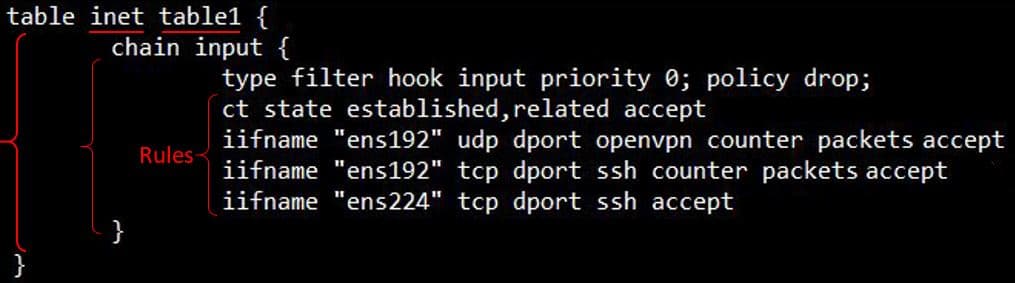
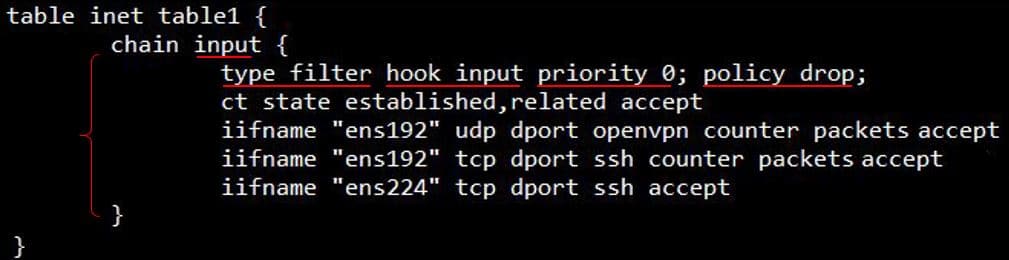
Chains are a container of rules and are located inside a table created beforehand. Chains can be a base chain that can control packets destined into a node and has a hook whereas a non-base chain is a chain that is used for the organization of chains and has no hook hence no control over packets. Similar to a table, all operational activities can be done on a chain in addition to renaming a chain. Chains should be followed by a name and an open and a closed curly bracket. They also come with a type, a hook, a priority, and a policy that must be defined when creating a chain as shown in the next figure.
Chain chain-name { type <type> hook <hook> priority <priority> ; policy <policy> ; }
5.3.1 Chains types
Filter: This is a standard chain type and supports all address families namely ARP, bridge, IP, IP6, and inet and hooks.
Route: It supports only IP and IPv6 address families and only output hook. If relevant parts of the IP header have changed, a new route lookup is performed.
Nat: It can perform Network Address Translation, and only supports IP and IPv6 address families. prerouting, input, output, postrouting hooks are also supported.
5.3.2 Chains hooks
A Hook in a chain refers to a specific stage a packet is being processed through a Linux kernel-based on defined rules. These hooks are ingress, prerouting, input, forward, output, and postrouting and are explained in detail in the next section. Prerouting, input, forward, output, and postrouting hook can also support IP, IPv6, and inet address families. To support the arp address family, input, and output hooks can be used while for netdev family, ingress hook should be used.
Prerouting: All packets entering a node are processed by this hook. It is invoked before the routing process and is used for early filtering or changing packet attributes that affect routing.
Input: This hook is executed after the routing decision. Packets delivered to a local system are processed by this hook.
Forward: This hook also happens after the routing decision. Packets that are not directed to the local machine are processed by this hook.
Output: This hook controls the packets that are originated from processes in a local machine.
Postrouting: This hook is used for the packets leaving a local system after the routing decision.
Ingress (only available at the netdev family): Since Linux kernel 4.2, traffic can be filtered before layer 3 and way before prerouting, after the packets are passed up from a NIC driver.
To read the rest of the article, you need to purchase and download the ebook with the provided link below.
How to buy and download the digital file of Essential Linux?
Easillyy works with Paypal to facilitate the transaction process. After finishing the payment process which is straightforward and can be seen on the payment guideline page, the file will be automatically sent to your email. To finish the payment process, you only need to have a valid debit or credit card and provide your details.
| Ebook | A comprehensive guide to Nftables |
| File format | PDF (Digital file) |
| Version | First edition |
| Page | 13 pages |
| Price | $5 US |
| Payment method | PayPal (All credit and debit card) |
 |
References
Netfilter. (2014). What is netfilter? https://www.netfilter.org/
Nftables wiki. (2016). Main differences with iptables. https://wiki.nftables.org/wiki-nftables/index.php/Main_differences_with_iptables
Nftables wiki. (2017). What is nftable? https://wiki.nftables.org/wiki-nftables/index.php/What_is_nftables%3F

Be First to Comment